How we Detect Deceptive Scams in GCash in 2023

In the Philippines, GCash is a popular mobile wallet app that allows users to make payments, transfer money, and even invest. The site has gained a significant following because of its conveniences and features. In addition to the platform’s growth, deceptive scams are targeted at its users. Scammers employ a variety of methods in order to deceive users on GCash, and we will examine these methods in this article so that you can be aware of deception tactics and protect yourself from them.
It becomes more and more attractive for bad people to take advantage of other people as GCash acceptance increases. As technology makes it easy to take advantage of people, scams are more prevalent than ever. For instance, scammers may contact their victims through SMS, social media, email, or chat apps. The advent of digital technology has made life easier for everyone, including scammers, it seems.
What is GCash?
GCash is a widely used mobile payment app in the Philippines that allows users to perform various financial transactions, from sending money to paying bills. Its user-friendly interface and convenience have made it a favorite among many Filipinos. With the app, you can pay for goods and services, transfer money to friends and family, and even invest.
The popularity of GCash has grown significantly in recent years, and it has become an essential tool for many. The ease of transferring money and making payments through your smartphone has made GCash an integral part of modern Filipino life.
How we Detect Deceptive Scams in GCash: Variety of GCash scams
1. Common Deceptive Scams
As the use of GCash has grown, so has the creativity of scammers. It’s essential to be aware of the common deceptive scams that can target GCash users:
Misdirection and fear are the most common tactics used by scammers. Most of the time, this is a phishing scam, where the attackers trick a user into giving them information which allows them to hijack the user’s GCash account. They are as follows:
- Number associated with your GCash account or mobile phone
- MPIN
- OTP
Here are a few scam examples:
1. Phishing scams using email and SMS
Due to the ease of sending multiple messages at the same time, this type of scam is widely used. By using language that makes you paranoid or hasty, the message usually exploits fear or greed in the user. Consequently, your information is given away unintentionally.
Due to this problem, many banks have removed clickable links from messages.
In order to exploit the fear and paranoia of recipients, the following scams are used via email/SMS:
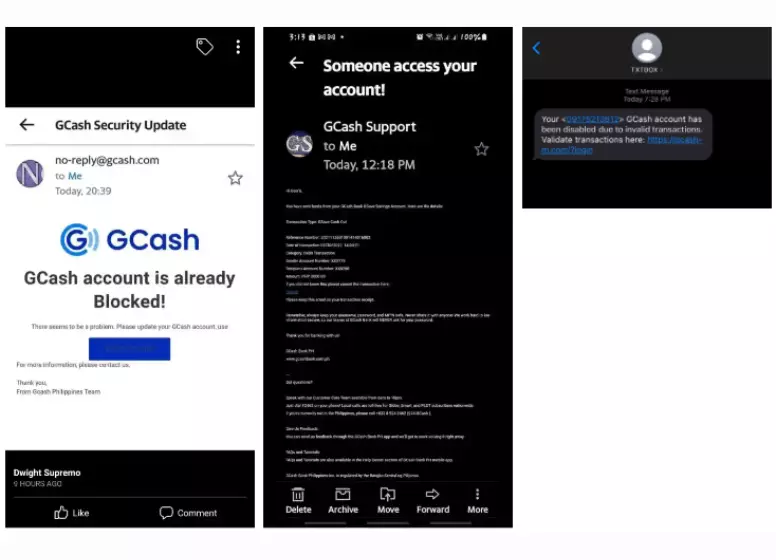
A user’s greed can be appealed to by emails/SMSs like these:
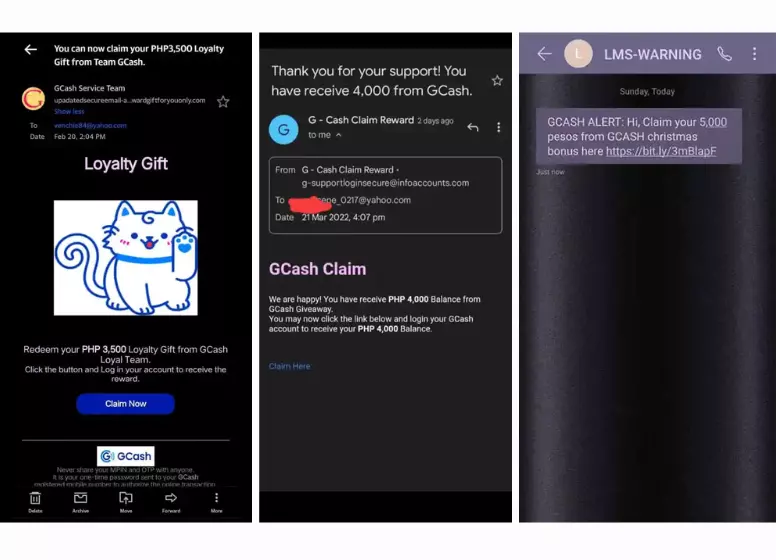
It is also common for scammers to pose as GCash by spoofing or fabricating the recipient’s email address or mobile number. A button or link usually appears with the message that redirects you to a form.
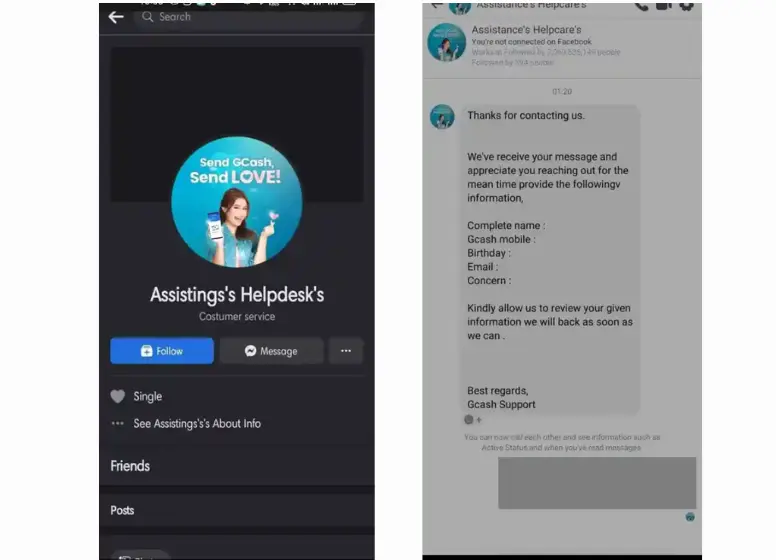
2. Phishing scams using messengers or chats
Facebook, Twitter, and other social media platforms have become popular with unwitting victims. To exploit their vulnerabilities, scammers typically use the platform’s private messaging function.
There are some ways to monitor GCash users, such as joining a Facebook group and looking for users who are facing account issues. Their next action is to take the user’s information, hijack their account and pose as GCash Support.
Due to the large number of grammatical errors these scammers use, these are easy to spot for more circumspect people. Furthermore, they cannot speak English very well, which makes them look like impostors, at best, or amateurs when compared to actual support agents.
The following is an example:
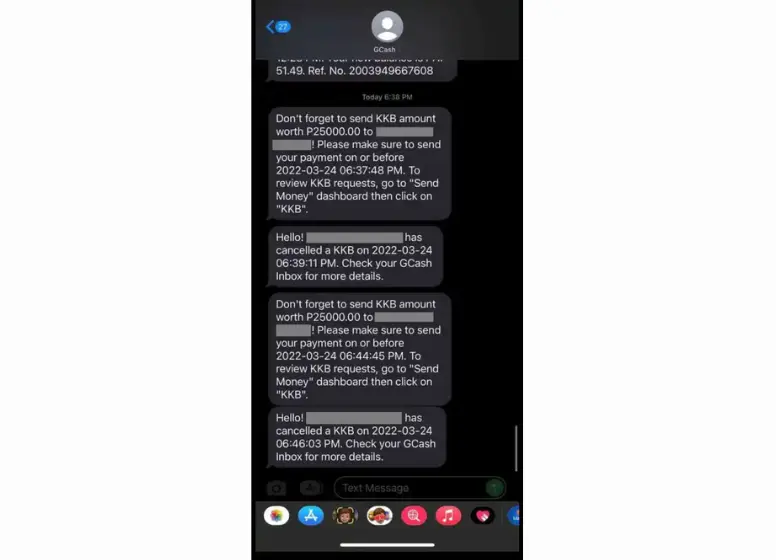
3. KKB Scams
A person can request funds from multiple people using KKB, a feature of GCash. Since the scammer does not need to go through a lot of technical stuff to execute this scam, it is easier to execute. KKB requests must be confirmed and money sent for the scam to succeed.
This method is commonly used by scammers to request loans. Preying on people’s needs or greed, they prey on their weaknesses. A scammer will often ask for collateral via the KKB feature when the user needs to borrow money or invest. He stops responding to the borrower once he gets the collateral.
By requiring Full Verification and OTP to be able to send money via KKB, the recent updates make KKB scams harder to pull off.
KKB requests such as the following are likely scams:
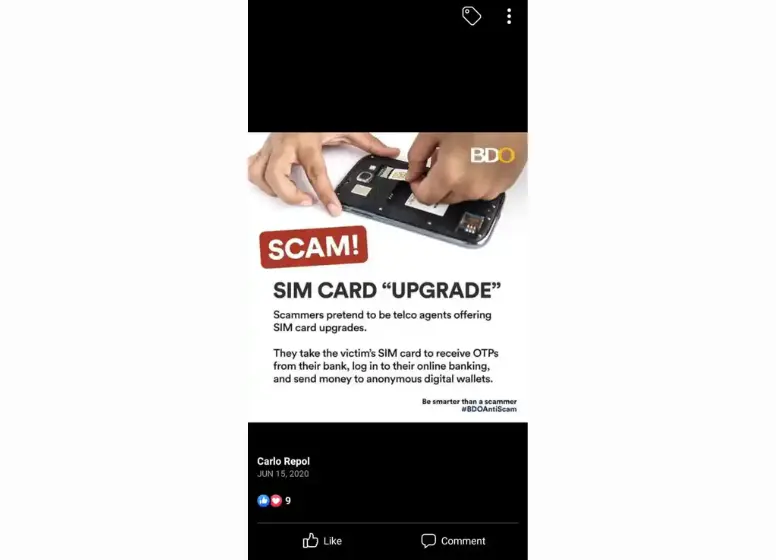
4. SIM Swap Scam
A SIM card is replaced using personal information also provided by the victim as part of the scam. The following banking advisories have been issued regarding this scam, including BDO’s:
Scammers impersonate telco support representatives to obtain personal information from victims. After obtaining this information, he impersonates the victim and requests that his phone line be disconnected. After presenting valid documents in the telco store, he can request a replacement SIM card.
Having the SIM card, he would be able to access many apps’ one-time passwords, including banking apps and financial apps. The MPIN is all he needs to use GCash. By filing a support ticket, he can impersonate the victim again. In addition, he could try to guess the MPIN, since many MPINs are simply birthdays or simple numbers.
Scammers will be able to take over all of your online apps as well as the money you have at their disposal with this method, which requires the most preparation.
5. Fake Promotions
Fake promotions or giveaways are set up by scammers, in which users are told they will receive nonexistent rewards in exchange for sending money to them.
6. Investment Schemes
It is not uncommon for scammers to lure users into their fake investment schemes by promising high returns, but they disappear with their funds after they get the money.
7. Unauthorized Transactions
You might be scammed by someone attempting to withdraw money from your GCash account without your consent. To minimize the damage caused by such transactions, it’s crucial to detect and report them as soon as possible.
How GCash Detects Deceptive Scams
As part of our commitment to security, GCash has implemented several measures to detect and prevent deceptive scams:
Advanced Security Algorithms
With GCash, unusual or suspicious transactions are detected using advanced security algorithms. By using these algorithms, potentially fraudulent activities can be identified quickly so that further investigation can be conducted.
User Behavior Analysis
Transaction patterns and user behavior are monitored by the app. An unusual transaction will be subject to additional scrutiny if it deviates significantly from your usual behavior.
Real-time Transaction Monitoring
Real-time transaction monitoring is provided by GCash. An unauthorized transaction can be temporarily halted if the system detects it, preventing further damage.
Reporting and Resolution
A user can easily report suspicious transactions or suspicious activities in GCash. Such reports are investigated and resolved promptly by their dedicated support team.
Steps to Protect Yourself
Even though GCash’s security measures are robust, its users are also responsible for protecting themselves from scams. You can take the following steps:
- To ensure you remain protected, keep your GCash app updated regularly.
- Make your account more secure by enabling two-factor authentication.
- It is always advisable to verify the authenticity of promotional offers and promotions before taking part in them. Usually, things seem too good to be true if they seem too good to be true.
- Sharing personal information should be done with caution. Passwords and sensitive information should not be shared with anyone, even if they claim to represent GCash.
A Guide to Avoiding Scams
As a result of the examples provided above, we should now be familiar with the different types of scams and what to look out for when we receive similar messages in the future. To be vigilant, we need to be critical of everything we receive in all types of correspondence.
GCash personnel will never ask you for your MPIN, since MPINs are private information. The majority of the time, you contact GCash Support rather than them contacting you.
When you go to an external site, always make sure you check its domain to see if it is legit. However, the bottom line is that if you are uncomfortable sharing your data, then don’t do it.
If I’ve been scammed, what should I do?
If this occurs, you should report it immediately to GCash Support, and your account will be frozen immediately. Unfortunately, you have a slim chance of reclaiming your funds. To stop these scammers from continuing to scam, GCash’s most likely action would be to blacklist the number.
Are there any Customer Protect cases I can report?
In some cases, yes. In others, no. The first thing you should do is to get in touch with the police as soon as possible, so they can gather as much evidence as possible.
What is the best way to track down a scammer?
Scammers transfer funds from your wallet to theirs as soon as they gain access to your account. Whenever he transfers or makes purchases using your account, you should receive SMS receipts.
What should I do if the scammer takes my money?
Getting your funds back is unlikely realistically. After receiving funds from you, an experienced scammer would transfer his funds to dummy accounts.
It is possible to get some of your funds back, however, if your case falls under Customer Protect.
What is the complaint procedure for GCash Support?
This form can be completed either from within the app or by filing a ticket. It is recommended that you provide as much evidence as possible.
Summary
Scams are also easier to spread due to today’s prevalence of technology. Phishing attacks are typically carried out through email or SMS, or via social media platforms such as Facebook. It is also common to fall victim to KKB scams when it comes to GCash.
When giving out personal information, we should always question whether it is warranted. It is never necessary to provide your MPIN to GCash support.
FAQs
How common are deceptive scams on GCash?
What should I do if I suspect a scam on my GCash account?
Are there any fees associated with reporting scams on GCash?
Can I recover my funds if I fall victim to a scam on GCash?
Is GCash safer than traditional banking for online transactions?
Here are the main features of GCash after reading what it is:
Money Transfers:
- Money Transfer using GCash
- Money From Wise to GCash
- Money From UnionBank to GCash
- Money From GrabPay to GCash
- Money from GCash to GrabPay
- Money Between Bank Accounts
- Money From GCash To GCash
- Money From ShopeePay To GCash
- Money From GCash To PayMaya
CAsh In, Cash Out:
New Features: